Internet of Things Automatic Security Testbed

Privacy-Preserving Detection of IoT Devices Connected Behind a NAT in a Smart Home Setup
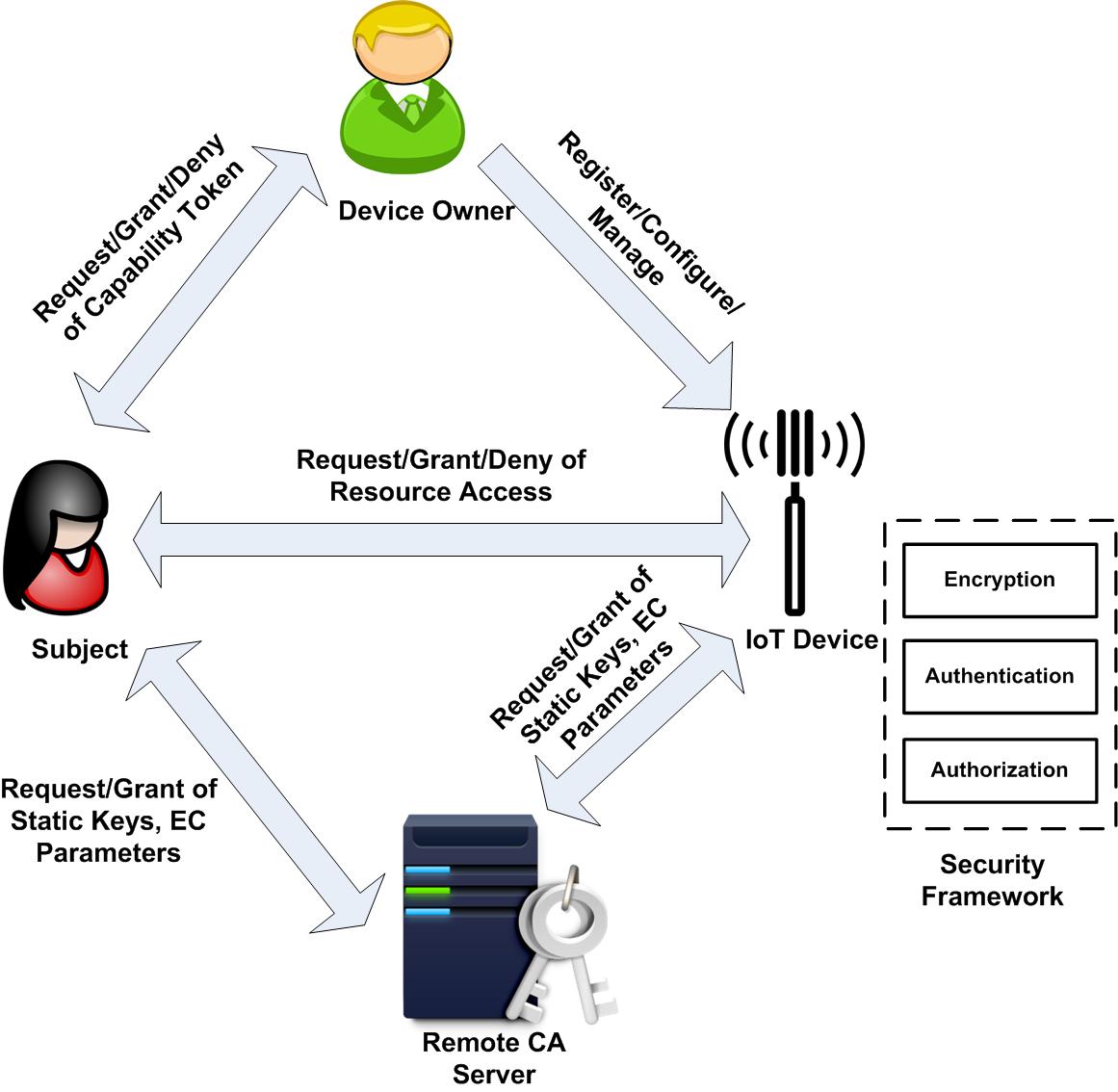
Decentralized Access Control for Internet of Things
This work proposes a decentralized security framework (comprising of both authentication and authorization mechanisms) for securing IoT systems. It is expected to address the scalability issue, facilitates decision making at the device level, and leverages machine-to-machine (M2M) communications to ensure end-to-end security. M2M communication is an essential feature for reducing human interventions and perceiving a smart environment. However, the challenge with decentralized approach is that we need to propose new authentication and authorization scheme which preserves device autonomy and also conforms to the resource-constrained nature of the IoT devices.
Thus, the broad scope of this work will be to design a decentralized, and light-weighted security framework for IoT devices, which enables establishment of secure communication channel, identity verification of requesting subjects (viz., smartphone app, or another device, or a remote server program), and make authorization decisions locally.
PIT: A Probe into Internet of Things by Comprehensive Security Analysis
Internet of Things Automatic Identification
Decentralized Localization and tracking in Wireless Sensor Networks.
Information Quality Aware Cross-layer Techniques in Wireless Sensor Networks
CoMiFin (Communication Middleware for Monitoring Financial Critical Infrastructure)
INSPIRE (INcreasing Security and Protection through Infrastructure REsilience)
Model for Understanding the Spread of Epidemics in Mobile Networks
Installing Asterisk and Interaction with SIP SER in UNITN (University Of Trento)
Secure Network Access Protocol (SNAP)
Embedded Hot Spot Information System
The project was my Bachelor’s final year industrial research project. The project is based on the localization and providing the position of the user.
Lexical Analyzer
STATUS (Net of sensors for asset management of server farm)